Featured
Table of Contents
7 Best Vpns For Tor Browser In 2023 (Do You Need One?)
Nevertheless, this is most likely just to be advised if you are a technologically advanced online user. Your browsing history and cookies are immediately reset when you stop using it. Tor prevents others from tracking the sites you check out. Tor attempts to make all users look-alike to stop anybody identifying you from the qualities of your browser or gadgets.

It is made up of websites that are just accessible through a Tor connection and can not be discovered through search engines like Google. The dark web is typically connected with wrongdoers which is why it's unlawful in some countries. If you wish to utilize the internet and leave no digital footprint, using the Tor browser is the very best solution.
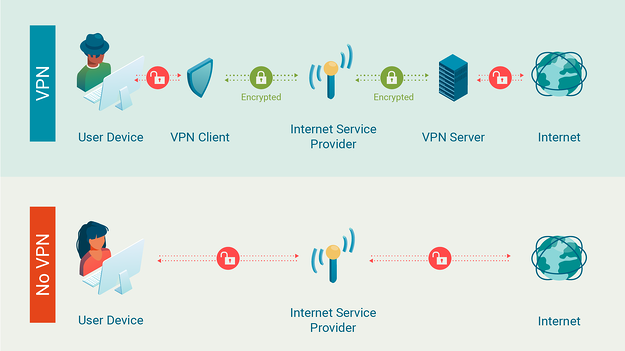
You can definitely utilize Tor for normal web surfing without a VPN. While not strictly restricted in many Western countries, the significant tech market players avoid motivating Tor internet browser use.
Using a complimentary VPN service might put your online security at risk. When you use a VPN server, you safeguard your traffic from being kept track of by your ISP.
Difference Between Tor Browser And Tor Over Vpn
Tor is a free browser that will encrypt your online activity, however it is slower, does not provide access to all sites, and can potentially lead to issues with the law. By Mary Atamaniuk Updated: Jan 21, 2021 15 min read Upgraded: Jan 21, 2021 15 min read A digital content writer passionate about tech, marketing, and cybersecurity.
While both tools can enhance your online privacy, they're as various as apples and orang ...
Tor Vs Vpn: What's The Difference And Which Is Better In ...

The Tor network can be used to utilized the regular InternetRoutine web it hides your IP address from everyone, everybody the consisting of operating individuals Running network itself, or the Dark Web, where everyone's Everybody address is hidden from everyone elseEverybody When you utilize Tor, your traffic connects to the Internet through a "Circuit", a collection of 3 computers, or Tor "nodes" that is changed every 10 minutes.
This avoids anyone from sleuthing on your it, consisting of the majority of the Tor network itself. Each computer system in a Circuit peels back one layer of encryption, to expose information that just it can see. They work like this: The is where your traffic enters the Circuit. It can see your IP address and the IP address of the middle node.
Theis where your traffic leaves the Circuit. It can see the IP address of the middle node and your traffic's destination. The Exit Node behaves a bit like a VPN, so any service you use on the Web will see the Exit Node's IP address as the source of your traffic.
The most uncomplicated way to utilize the Tor network is through the Tor Internet browser. All you have to do is download and set up the latest variation from the main website and utilize it like a routine web browser. There is no knowing curve; the Tor internet browser is based on Firefox and is as easy to use as any browser.
Can A Vpn Server Be Traced Through Tor?
Your traffic joins the Web from the VPN company and uses your VPN supplier's IP address, so it appears to stem there. Here are some important differences in between the two innovations: There are many VPN services to choose from, there is only one Tor network. A VPN assumes you trust your VPN provider.
Your VPN provider aims to provide a connection that is fast and steady. Tor aims to provide a connection that is resistant to sophisticated attacks. VPN provider are usually run by organizations answerable to local laws. Tor is run by volunteers who can't see what is travelling through their servers.
If you've ever wanted to alter your IP address to gain access to content from another location in the world, you have actually most likely come throughout proxy servers, VPNs and Tor. This post will assist you decide in between a VPN vs proxy vs Tor to safeguard your online activity.
A VPN will alter your IP address and secure your web connection, offering you the greatest level of defense. We'll discuss what those are and how VPNs, proxies and Tor compare.
Vpn, Proxy Or Tor: What's The Difference And What's Best?
A VPN will usually be faster than a proxy server if you're using an excellent quality VPN. The VPN customer would secure your data and send it to the VPN server, which would then send it to the proxy server.
To that end, we'll describe what proxy servers, VPNs and the Tor network do and how they work. We'll talk about how and when you ought to use them to assist you choose the finest service for your use case. Between a proxy vs VPN vs Tor, it's clear to us that a VPN connection is the fastest and most protected.
Latest Posts
Best Vpns For Business Travelers To Stay Digitally Fit (2023)
The Best Mobile Vpns Of 2023
Best Mobile Vpn 2023